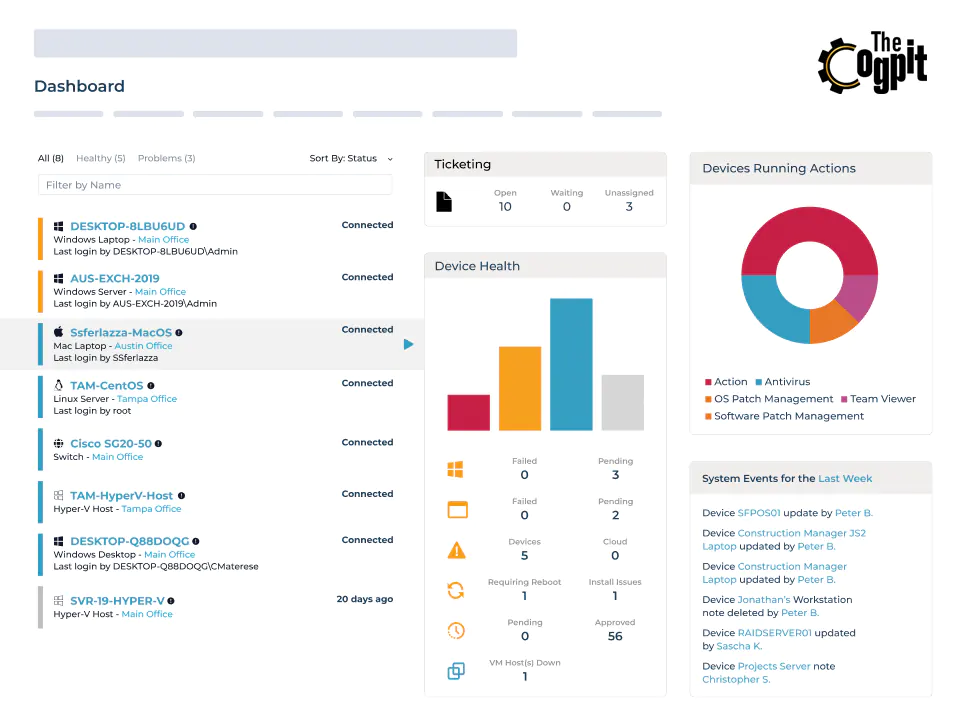
Having all of the Cogs enabled will give you automatic access to The Cogpit. It functions as a front-row seat to everything going on within your establishment. All of the individual reporting segments are aggregated and displayed here, giving you a unique insight into the lifeblood of your company and the work that’s being done.
The dashboard of the beating heart of our system, from here you can review all reports from every cog as they’re being forwarded with additional report templates, an import function and so much more.